Understanding Proxies and Mobile Proxies: A Comprehensive Comparison
Discover the differences between traditional proxies and mobile proxies, including their unique advantages, trust levels, and use cases. Learn how each type of proxy can enhance your online privacy, security, and efficiency.
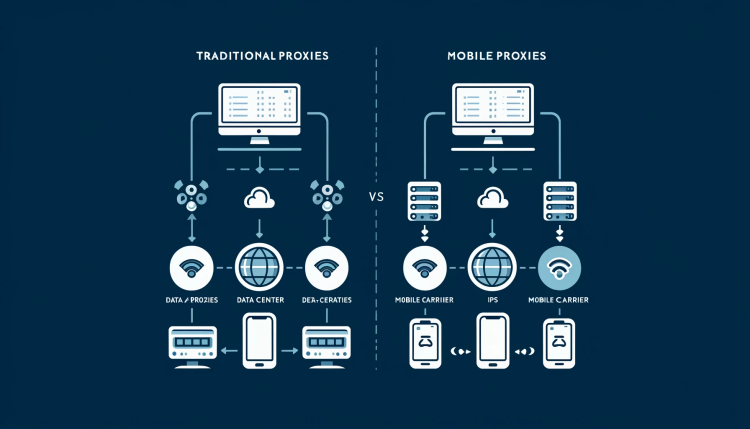
In today's digital age, online privacy and security are paramount. One of the essential tools for maintaining privacy and enhancing security is the use of proxies. Proxies serve as intermediaries between a user's device and the internet, masking the user's IP address and providing anonymity. This article delves into the specifics of traditional proxies, mobile proxies, and compares their functionalities and use cases.
What is a Proxy?
A proxy server acts as a gateway between your device and the internet. When you connect to a proxy, your internet requests are routed through the proxy server. This process hides your original IP address, making it appear as though your traffic is coming from the proxy server's IP. Proxies are commonly used for various purposes, including:
- Anonymity: Concealing the user's real IP address to protect their identity online.
- Access Control: Allowing or blocking access to specific websites or services based on user policies.
- Bypassing Geo-Restrictions: Accessing content that is restricted in certain geographic locations.
- Web Scraping: Automating data collection from websites without getting blocked.
What is a Mobile Proxy?
Mobile proxies operate similarly to traditional proxies but with a key difference: they use IP addresses associated with mobile devices. These proxies route traffic through mobile networks, using IPs assigned by mobile carriers. This distinction offers several unique advantages:
- Higher Trust Levels: Mobile IPs are generally trusted more by websites and services compared to data center IPs, reducing the likelihood of being flagged or blocked.
- Dynamic IPs: Mobile proxies often provide rotating IP addresses, enhancing anonymity and making it harder for websites to track usage patterns.
- Geolocation Flexibility: They offer the ability to appear as though you're accessing the internet from various locations, depending on the mobile carrier's IP range.
Comparing Proxies and Mobile Proxies
1. Trust and Reputation
- Traditional Proxies: Often use data center IPs, which can be easily identified and blocked by websites. These IPs are more likely to be flagged due to their frequent use for automated tasks like web scraping.
- Mobile Proxies: Utilize IPs from mobile carriers, which are generally more trusted. This reduces the chances of detection and blocking, making mobile proxies ideal for tasks requiring high trust levels.
2. IP Rotation and Anonymity
- Traditional Proxies: May offer static or rotating IPs, but static IPs can be quickly flagged. Rotating proxies help, but they may still come from a limited IP pool.
- Mobile Proxies: Frequently rotate IPs due to the nature of mobile networks. This dynamic rotation enhances anonymity and reduces the risk of detection.
3. Cost and Availability
- Traditional Proxies: Typically more affordable and widely available. They are suitable for general purposes where high trust is not a priority.
- Mobile Proxies: Generally more expensive due to their higher trust level and IP rotation capabilities. They are ideal for sensitive tasks like ad verification, social media management, and accessing restricted content.
4. Use Cases
- Traditional Proxies: Suitable for web scraping, bypassing geo-restrictions, and basic anonymity needs. They are also used for corporate networks to control and monitor internet usage.
- Mobile Proxies: Preferred for tasks requiring higher trust and dynamic IPs, such as social media automation, ad verification, and accessing mobile-specific content.
Conclusion
Both traditional proxies and mobile proxies have their unique advantages and are suited for different purposes. Traditional proxies are cost-effective and sufficient for general use, while mobile proxies offer higher trust levels and better anonymity, making them suitable for more sensitive tasks. Understanding the differences and choosing the right type of proxy based on your needs can significantly enhance your online activities and security.
For more detailed reviews and recommendations on the best proxy services available, visit lonake.com. Our expert reviews will guide you in selecting the most suitable proxy service for your specific needs.
What's Your Reaction?